Bringing Precision
& Speed to SecOps
& Speed to SecOps
Cybersecurity operations have a fundamental weakness brought on by the sheer volume of event data available for analysis. That is, it’s extremely difficult to understand what’s normal, what’s an outlier, and what truly needs to be addressed right now. Auguria transforms data into actionable knowledge with machine speed comprehension and the denoising of vast quantities of security event data.
The Auguria Security Knowledge Layer™ (SKL) is an innovative solution serving as a high-performance, agnostic translator that interlinks all security data wherever it lives. Auguria SKL™ enriches data using a novel AI approach so as to make it more usable to human analysts fighting on the front lines of SecOps as well as for input to AI LLM copilots initiatives.
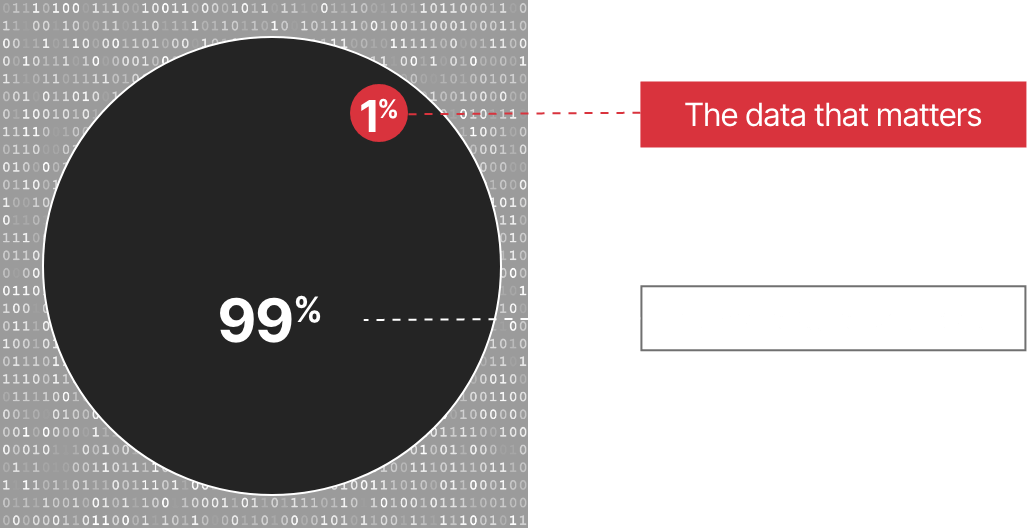
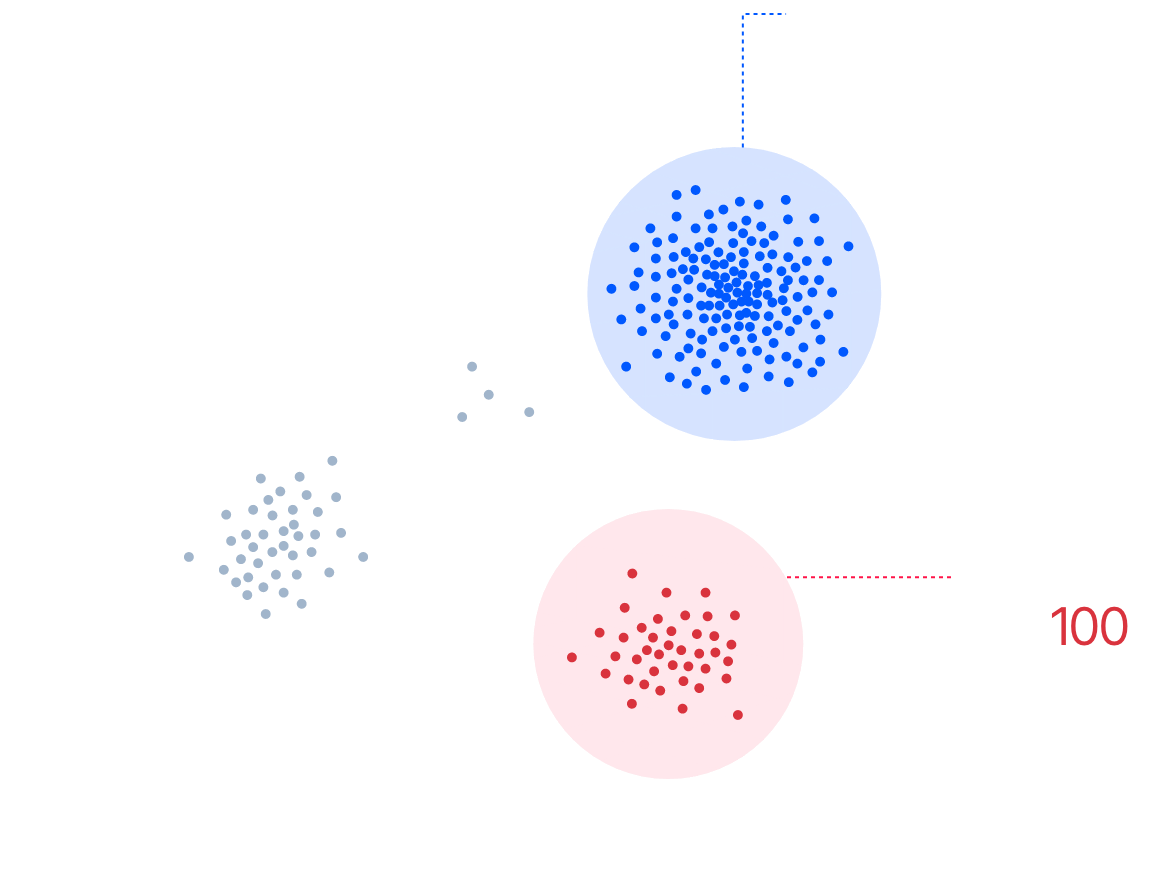
Studies show that ⅓ or more of analyst time is spent chasing shadows within benign data (IBM).
Auguria empowers analysts to reclaim time by revealing the <1% of data that typically matters.
The Auguria SKL™ Platform
Key Benefits

Graduate to AI Grounded in Human Expertise
Not all AI is created equally. Auguria is encoding generations worth of hard-won human DFIR experience into AI models capable of cutting through a sea of multi-vendor event data. By synthesizing AI with human skill, Auguria SKL applies expert-level security knowledge to focus analysts on what’s truly important. Auguria is AI to empower people.

Transform Security Data into Knowledge
Auguria is not just a tool; it’s a transformative element of the security operations tech stack. All data traversing Auguria’s Security Knowledge Layer is ranked semantically and assigned a priority along a spectrum from normal to highly unusual. Everything is mapped to a comprehensive ontology to provide human operators valuable relational context for informed decision making.

Denoise 100% of Security Data with Automation
Auguria’s inline ingestion and prioritization brings clarity to petabytes of inbound data per hour. SecOps no longer has to expend effort wading through data seeking critical clues because Auguria SKL separates all that is normal from everything else all in near real time. This enables analysts to focus on the 1% that matters.

Find the
Unknowns
Unknowns
Auguria helps SecOps gain the superpower of spotting previously unknown, novel activity. We do this fully automatically by first eliminating known knowns and classifying benign and routine activity. What remains uncovers the unknown, pinpointing true outliers.

Skip the
Black Box
Black Box
All Auguria decisions are explainable. Our aim is to foster trust through transparency. All classified and ranked data is mapped onto our Security Knowledge Layer ontology for easy reference with an accompanying justification for its assignment.

Gain Immediate
Context
Context
Results are available immediately within Auguria SKL and are dispatched back into your analytics infrastructure. The choice is yours. The Auguria SKL applies the human DFIR experience via its AI models automatically with no manual data rules engineering required.
How It Works
The Auguria platform is built on a flexible framework that adapts to each customer’s operational model and
avoids costly, inefficient vendor lock-in.
avoids costly, inefficient vendor lock-in.

Deploy on Your Terms
Decide which sources of data you want enriched. Select one, several or many. The more complex, data rich, and “noisy” the better. Expand to other sources as you gain comfort. Auguria’s ease of deployment allows customers to initially apply our tech to a subset of their data so they can realize value in a low friction way.
Ingest Data Where It Lives
Auguria connects to and ingests data where it lives and from where it originates including SIEMs, XDRs, Data Lakes, and APIs. Our observability-like data wrangling ecosystem offers multiple ways to initiate pulls and receive pushes out-of-the-box:
-
3rd party API connectors
-
HTTP webhooks
-
S3 and other cloud object storage
-
JSON, Parquet, ORC, CSV, and more
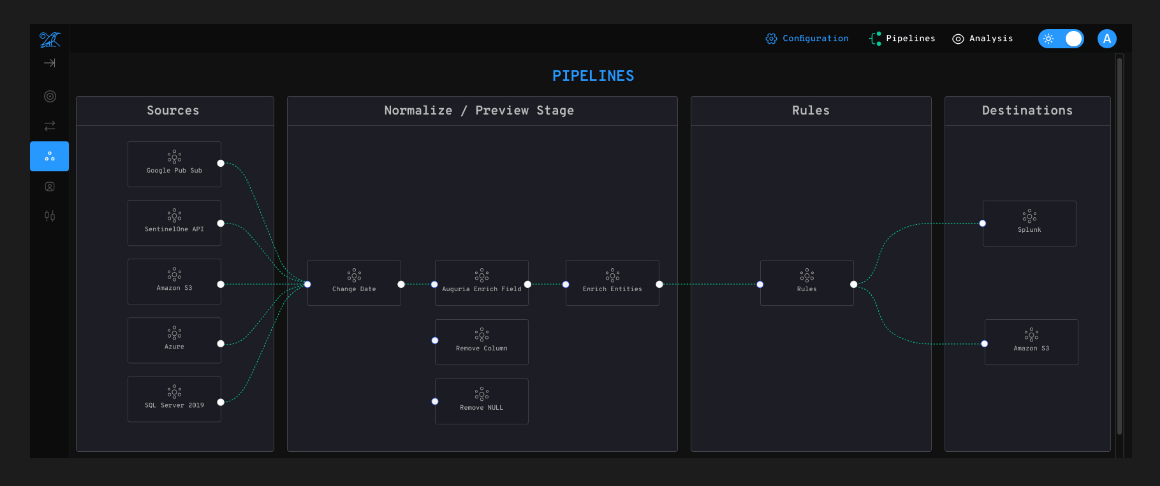
Normalize Everything, Discard Nothing
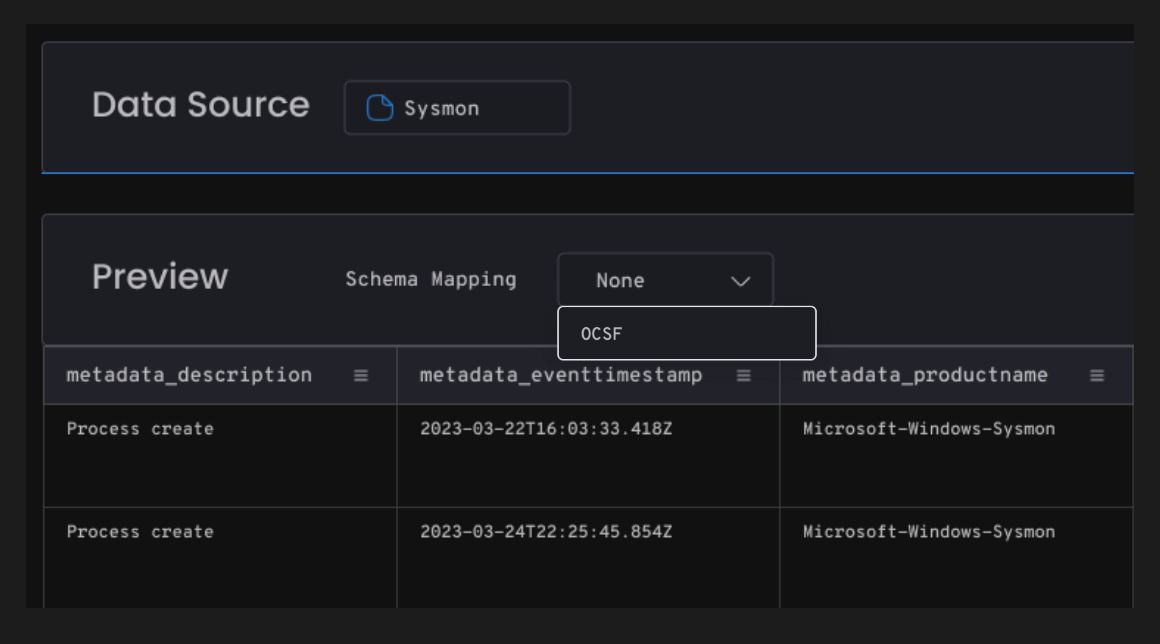
All incoming data is optimized by standardizing and normalizing it automatically to OCSF schema and timelines with Auguria’s no-code ETL workflow editor — an intuitive, spreadsheet-inspired workbench that makes data management as simple as using Excel®. Auguria classifies every event, giving you the choice to divert and store that data in less costly buckets vs. having it overwhelm your expensive, high performance analytical platforms.
Enrich Every Event
Auguria AI models are deeply “grounded” by encoding real-world, human security knowledge. This key differentiator provides our AI with an intrinsic understanding of the relationships among security events. Every event in every data stream is assigned an appropriate priority score in near real time and at petabyte per hour scale. Likewise, all data is assigned a place within Auguria’s Security Knowledge Layer ontology map with an accompanying rationale for its assignment.

Gain Immediate Clarity
Comprehend your data in ways never before possible within the Auguria platform or via SKL-enriched data dispatched back to your existing analytics platforms. This is the beauty of Auguria SKL enrichment. The most voluminous and complex data is now summarized and presented intuitively in a manner that will surface answers to security questions that often no one knows how to ask in the first place. Security analysts benefit by renewed confidence of quickly knowing which events should be prioritized and how to interpret them.
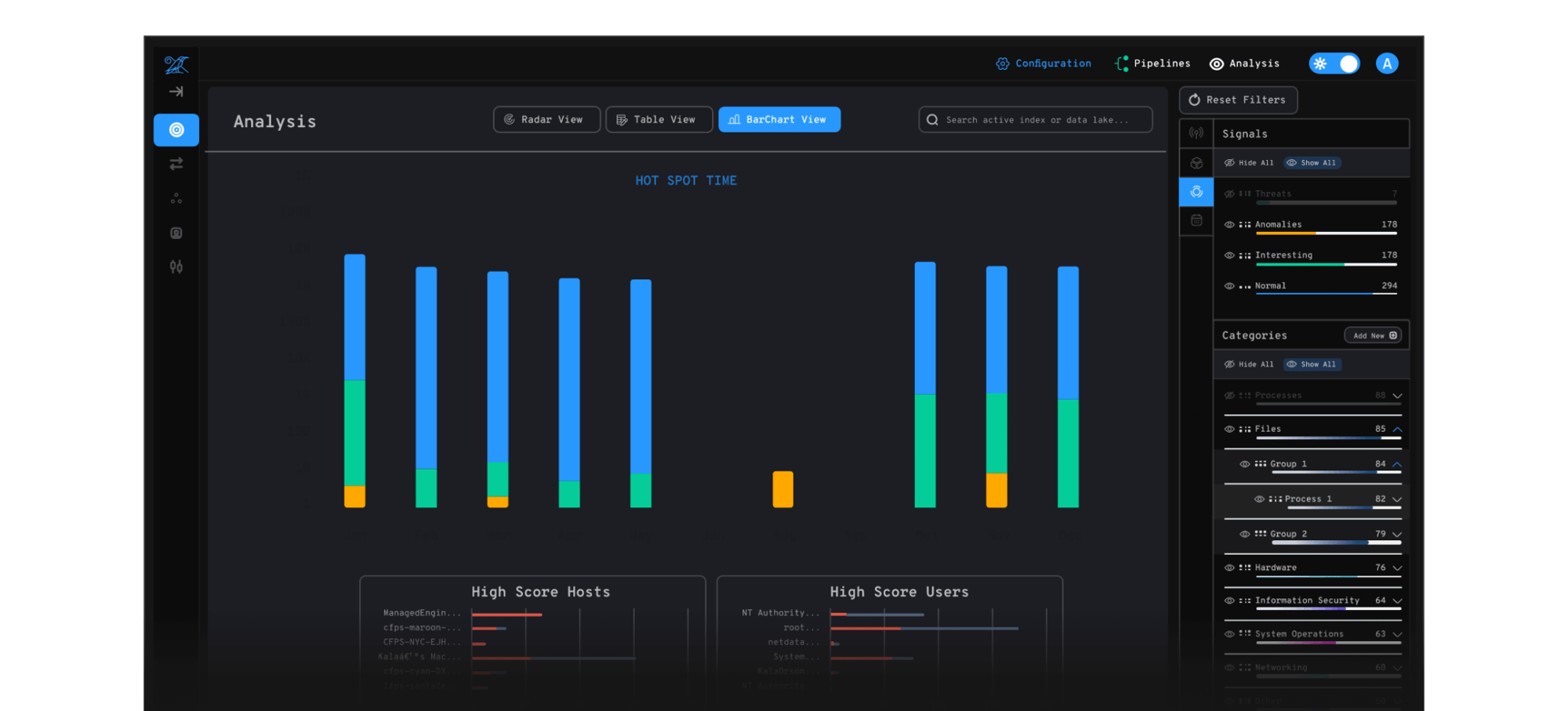
Our visual data radar chart supercharges exploratory data analysis. Data priorities can now make sense at scale and arm analysts with the insight to effortlessly design automation and analytics workflows for advanced detection engineering, and guided threat hunting.
Automate with New Insight
Automate the downstream data journey of every single event, now enriched with Auguria’s insight, by
having powerful but simple metrics to key in on. The use cases are numerous. The benefits are immense.
having powerful but simple metrics to key in on. The use cases are numerous. The benefits are immense.
Here are a few examples:
-
Divert redundant data from expensive SIEM storage to cheaper S3 buckets.
-
Feed your AI in the preferred language of machines using our pre-computed vectors.
-
Tune alert handling by precisely knowing which alerts are false positives and which are high priority, while also having the insight to know how similar alerts were handled in the past.
-
Query data by sifting through the noise using simple, universal prioritization criteria.
-
Generate optional logic rules using data output examples.
-
Enable your compliance team to intelligently and confidently reach final disposition on data by value rather than time.
Event: “powershell -EncodedCommand “VwByAGkAdABlAC0ATwB1AHQAcAB1AHQAIAAiAFkAbwB1ACAAdwBpAGwAbAAgAG0AYQBrAGUAIABtAGUAIABwAGEAbgBjAGEAawBlAHMAIgA=” Category: “Processes” User/Host: SYSTEM / ASCLTCWKKKN0 Justification: The log shows the execution of a temporary installer file. Score: 100 (Anomaly)
Event: “powershell -EncodedCommand “VwByAGkAdABlAC0ATwB1AHQAcAB1AHQAIAAiAFkAbwB1ACAAdwBpAGwAbAAgAG0AYQBrAGUAIABtAGUAIABwAGEAbgBjAGEAawBlAHMAIgA=” Category: “Processes” User/Host: SYSTEM / ASCLTCWKKKN0 Justification: The log shows the execution of a temporary installer file. Score: 100 (Anomaly)
Event: “powershell -EncodedCommand “VwByAGkAdABlAC0ATwB1AHQAcAB1AHQAIAAiAFkAbwB1ACAAdwBpAGwAbAAgAG0AYQBrAGUAIABtAGUAIABwAGEAbgBjAGEAawBlAHMAIgA=” Category: “Processes” User/Host: SYSTEM / ASCLTCWKKKN0 Justification: The log shows the execution of a temporary installer file. Score: 100 (Anomaly)
Event: “powershell -EncodedCommand “VwByAGkAdABlAC0ATwB1AHQAcAB1AHQAIAAiAFkAbwB1ACAAdwBpAGwAbAAgAG0AYQBrAGUAIABtAGUAIABwAGEAbgBjAGEAawBlAHMAIgA=” Category: “Processes” User/Host: SYSTEM / ASCLTCWKKKN0 Justification: The log shows the execution of a temporary installer file. Score: 100 (Anomaly)
Event: “powershell -EncodedCommand “VwByAGkAdABlAC0ATwB1AHQAcAB1AHQAIAAiAFkAbwB1ACAAdwBpAGwAbAAgAG0AYQBrAGUAIABtAGUAIABwAGEAbgBjAGEAawBlAHMAIgA=” Category: “Processes” User/Host: SYSTEM / ASCLTCWKKKN0 Justification: The log shows the execution of a temporary installer file. Score: 100 (Anomaly)
Key Features
Pipelines Made Easy
Integrate event data from leading EDR, identity, network, cloud, and other products using Auguria’s comprehensive No-Code ETL connectivity suite. Format and transform rich security data flows using an intuitive data workbench. If you know how to use a spreadsheet, you can use Auguria.

Exploratory Visualization
See the top 1% of AI-prioritized enrichments come alive within Auguria’s interactive data radar that plots the most impactful security incident and threat hunting clues onto an easy-to-understand ontology chart.

Cloud and Tool Agnostic
Auguria evaluates and enriches all incoming data so that it can be used within Auguria’s native platform or within other analytics platforms (Splunk® etc).

Flexible Deployment
Auguria SKL is built on Kubernetes and is cloud and data center agnostic. Run Auguria where your data lives.
SECURE EARLY
ACCESS
ACCESS
Are you ready to set a new standard for your SecOps team?
Auguria is inviting interested organizations to apply for early access to the platform. If you’re eager to see Auguria in action, we encourage you to get in touch using the form below.
This site is protected by reCAPTCHA Enterprise and the Google Privacy Policy and Terms of Service apply.